On Security Headers in HTTPS

I am happy to report this site has received an A+ rating for its HTTP security header implementations.
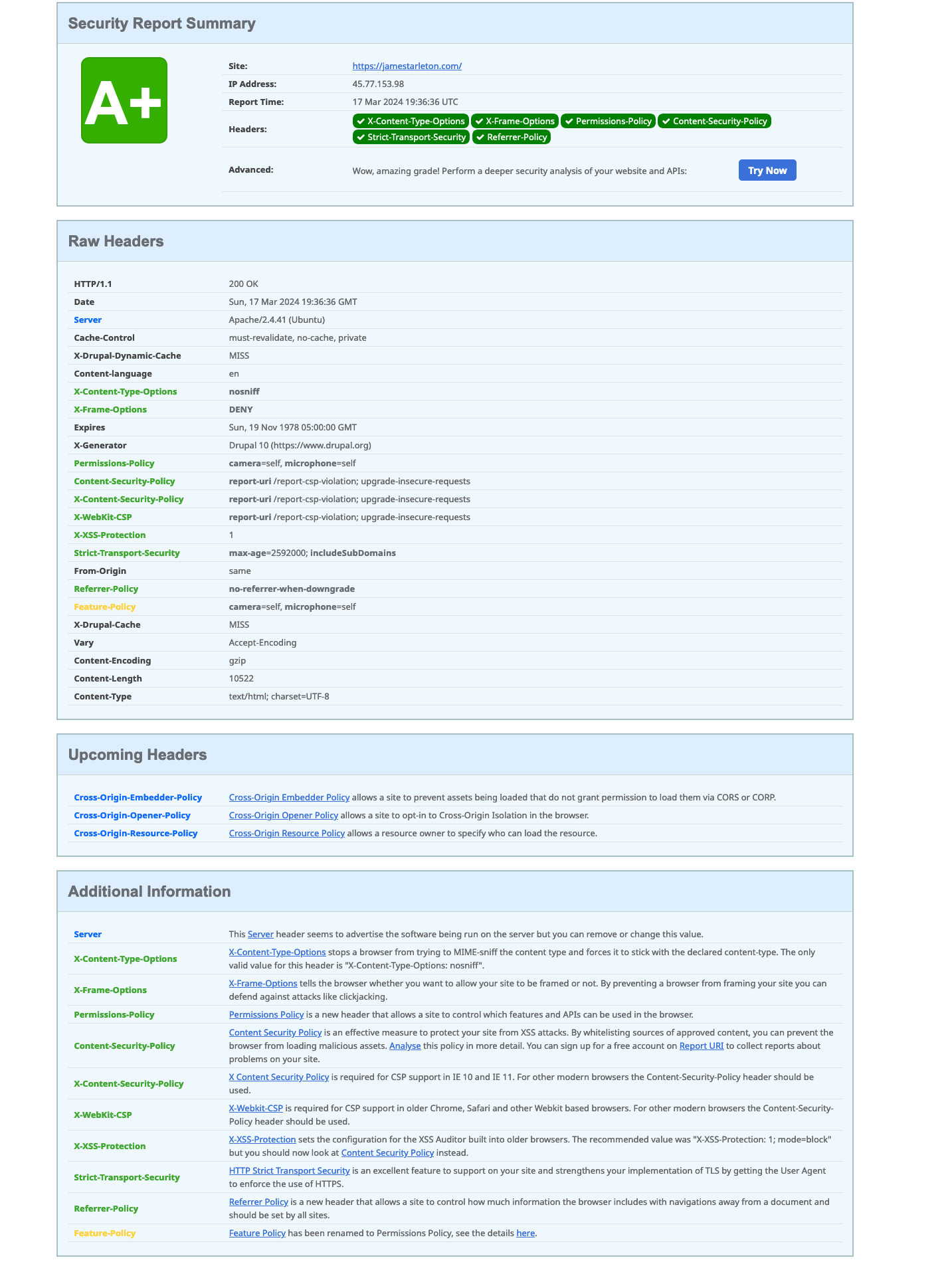
I found a very nice article on HTTP security headers here, but I could only find three of four articles in the series.
These articles look like they cover nearly everything one might need to know about HTTP security headers.
Along with handy testing tools such as https://securityheaders.com, I feel my site is close to being all set in terms of closing the most straightforward security header gaps.
I hope the author publishes another installment and addresses the Content-Security-Policy header too, as that one in my experience is somewhat difficult to get exactly right. Even when configured for "report only" it seems to have a bad habit of being too strict to serve your web application reliably, blocking images, critical stylesheets and javascripts, interfering with the basic loading of responses, and so on, if implemented incorrectly.
The allowed list and correct CSP header is an ever-evolving value, since you have to not only determine all your site's external dependencies (any CSS, JS, and images hosted on Google, Google Analytics, for example) but also any dependencies of those dependencies and so on. The point of this security header is to lock down the site from making unexpected HTTP requests to external resources. But to also account for the fact that in any web application, some external dependencies are going to be required.
Recent content
-
8 hours 19 minutes ago
-
1 day 6 hours ago
-
1 day 10 hours ago
-
2 days 2 hours ago
-
5 days 11 hours ago
-
1 week 2 days ago
-
1 week 4 days ago
-
1 week 4 days ago
-
1 week 4 days ago
-
1 week 4 days ago

